+7 (812) 929-8283
FibeAir® 1500P - Advanced Encryption Solution
EncryptAir™ - The First Built-In High-Capacity Encryption Solution
Due to the growing demand to enhance information security over the PTP wireless link, Ceragon Networks implemented the solution of adding another layer of protection against eavesdropping on the wireless signal and unauthorized access to the rooftop. Our proprietary solution is a system that enables the highest level of information security over the wireless medium, without degrading link performance.
The unique solution was integrated in FibeAir products, introducing the first carrier class encrypted PTP wireless link. When FibeAir is configured with encryption, data received from the line interface (plain text) is coded, and sent via the radio. The remote site will receive the data in its coded form, decode it back to plain text, and then send it on through the line to the user.
The encryption used is the AES (Advanced Encryption Standard) algorithm, as specified by the FIPS 140-2 Level 2 Security standard. AES is a symmetric block cipher that can encrypt (encipher) and decrypt (decipher) information. When encryption is enabled, FibeAir automatically sets up the required keys.
Wireless Encryption
Wireless connections are complex to encrypt. The need to overcome BER and fading in the radio channel, while maintaining the radio system performance, requires special handling.
The plain data passing through the FibeAir IDU is encrypted and transmitted to the ODU. The encrypted data protects the information against potential eavesdroppers.
Ceragon’s robust encryption mechanism employs the AES algorithm, which is more suitable for wireless medium, while maintaining the field-proven FibeAir system quality performance.
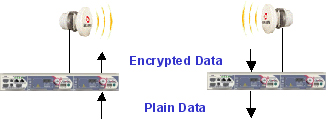
Ceragon’s Encryption Method
Ceragon’s encryption is based on proprietary Ceragon Networks technology and provides the first high capacity (120 Mbps) wireless encryption connection. The method implements the AES (Advanced Encryption Standard) algorithm, which uses symmetric encryption keys, a common secret between source and target, in order to encrypt/decrypt the data. It also implements proprietary algorithms that enable the highest level of information privacy. Once established, each link has a unique set of encryption keys, allowing many links to operate in the same area, with no link intercepting the data of another link.
With 2^256 possible keys, the possibility of discovering a particular key is extremely unlikely when typical eavesdropping techniques are used. If the key is changed frequently, the risk of its discovery is diminished even further. Unique Ceragon protocols were designed to generate secret keys and keep them safe and undiscoverable.
Ceragon’s encryption algorithm consists of random key generation, frequent key replacement, and a unique set of keys for each link, for operation in a dense wireless environment. The key consists of 256 binary digits (0s or 1s), all of which are used by the encryption algorithm.
Integrated in the FibeAir IDU, the encryption algorithm is completely transparent to the operator, functioning automatically without the need for manual key loading or replacement.

